Power distribution systems are important for keeping our electricity flowing smoothly. But as we make them smarter with digital technology and the Internet of Things (IoT), they become vulnerable to cyberattacks. These attacks can disrupt their operation and cause damage. One type of attack that’s particularly concerning is false data injection (FDI). This is when hackers insert fake information into the system to mess things up. Other attacks, like denial of service (DOS), distributed denial of service (DDOS) and GPS spoofing, can also cause trouble. In this blog, we’re going to look at ways to defend against false data injection attacks and keep our power grids safe. We’ll explore different methods for detecting and stopping false data injection cyberattacks.

Table of Contents
ToggleUnderstanding of false data injection (FDI) attacks:
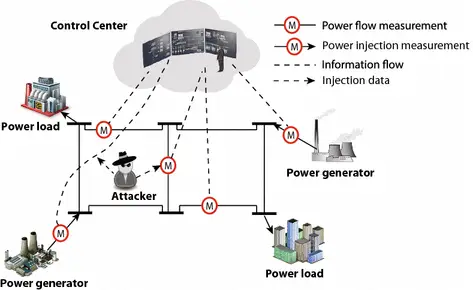
False data injection (FDI) attacks are a type of cyber assault where attackers manipulate the data within a system by inserting fake or misleading information. In the context of power systems, false data injection attacks involve injecting falsified data into the smart grid infrastructure, such as altering sensor readings or control signals. These attacks aim to deceive the system’s decision-making processes, leading to incorrect actions or decisions that can disrupt the normal operation of the grid. False data injection attacks exploit vulnerabilities in the communication channels, sensors, and control mechanisms of the smart grid, posing a significant threat to the reliability and security of power distribution networks.
The Risk of FDI Attacks on Smart Grids
FDI attacks present a significant threat to the integrity and reliability of smart grids. By injecting false data into the system, attackers can deceive the grid’s control mechanisms and decision-making processes, leading to potentially severe consequences. These attacks can cause grid instability, disrupt power distribution, and even result in blackouts. Furthermore, False data injection attacks can compromise the trustworthiness of data used for monitoring and control purposes, undermining the overall security and resilience of the smart grid infrastructure. Therefore, addressing the threat posed by False data injection attacks is essential to ensure the continued operation and safety of power distribution systems.
Characteristics of FDI attacks
False Data Injection (FDI) attacks involve the malicious insertion of fabricated or misleading data into a system, with the intent to deceive and disrupt normal operations. In the context of smart grids, False data injection attacks target the integrity of data used for monitoring, control, and decision-making processes within the power distribution network.
Characteristics of FDI attacks include:
- Deception: It aim to deceive the system by injecting false information that appears legitimate, leading to incorrect decisions and actions.
- Manipulation: Attackers manipulate critical parameters such as power flow, voltage levels, and load distribution by injecting falsified data into sensors or control signals.
- Covert: It can be difficult to detect as the falsified data may closely resemble legitimate readings, making it challenging to distinguish between genuine and manipulated information.
- Targeted: It specifically target vulnerabilities within the smart grid infrastructure, exploiting weaknesses in communication channels, sensors, and control mechanisms.
- Disruption: The ultimate goal of False data injection attacks is to disrupt the normal operation of the smart grid, potentially causing grid instability, power outages, and financial losses.
Methods and techniques used by attackers to inject false data:
Attackers employ various strategies to inject false data into smart grid systems, exploiting vulnerabilities in communication channels, sensors, and control mechanisms. Some common methods and techniques include:
- Man-in-the-Middle (MitM) Attacks: In MitM attacks, attackers intercept communication between devices in the smart grid network and inject false data into the transmission. By inserting themselves between the sender and receiver, attackers can modify data packets in transit, leading to the propagation of falsified information throughout the network.
- Sensor Tampering: Attackers physically tamper with sensors installed within the smart grid infrastructure to manipulate the data they collect. This may involve altering sensor calibration, bypassing authentication mechanisms, or directly modifying sensor readings to inject false information into the system.
- Software Exploitation: Attackers exploit vulnerabilities in software systems used within the smart grid network to gain unauthorized access and manipulate data. This can include exploiting software bugs or weaknesses in authentication mechanisms to inject falsified data into control systems or data repositories.
- Insider Threats: Insiders with privileged access to smart grid systems may intentionally inject false data for malicious purposes. This could be motivated by financial gain, sabotage, or espionage, posing a significant threat to the integrity and security of the smart grid infrastructure.
Victim Devices / System and its solution
State Estimator:
State estimator serves as a vital component for monitoring and managing the electrical network’s operations. It’s a computational algorithm or tool that utilizes data from various sensors and measurements scattered across the grid to estimate the current state of the system.
Type of Attack: Power Buses and Sensors
Description: This attack involves manipulating the power flow measurement within the state estimator, creating inconsistencies in the data collected from power buses and sensors.
Solution: To address this issue, the proposed solutions include using advanced techniques such as Convolutional Neural Network (CNN) and Cumulative Sum Algorithm (CUSUM) to detect anomalies and ensure the integrity of power flow measurements.
SCADA System:
It serves as a central nervous system, collecting real-time data from various sensors, meters, and devices distributed throughout the grid infrastructure.
Type of Attack: Power Measurement, Grid State Transition
Description: Attackers manipulate power measurements and grid state transitions within the SCADA system, leading to inconsistencies in grid parameter readings and fake grid states being presented to operators.
Solution: To mitigate these attacks, a combination of quick intrusion detection algorithms and short-term state forecasting models is proposed. These solutions aim to rapidly detect intrusions and predict future states to prevent disruptions to the grid’s operation.
Smart Grid:
Type of Attack: Dynamic Load Altering, Power Bus
Description: This attack involves altering dynamic loads and power bus parameters within the smart grid, leading to disruptions in load control and distribution.
Solution: To counteract these attacks, an adaptive sliding load control model is proposed. This model dynamically adjusts load control mechanisms to respond to changing conditions, ensuring efficient and stable power distribution even in the presence of adversarial attacks.
Implications of False data injection (FDI) Attacks
Grid instability and potential blackouts:
FDI attacks can destabilize the smart grid, leading to disruptions in power distribution and potential blackouts. By injecting false data into the system, attackers can manipulate critical parameters, causing instability and compromising the reliability of the grid.
Compromised operations and decision-making:
It can compromise the integrity of data used for monitoring and control purposes within the smart grid. This can lead to incorrect decisions and actions by grid operators, resulting in suboptimal operation and potential safety risks.
Financial losses and economic impacts:
FDI attacks can have significant financial consequences, including direct costs associated with system downtime, equipment damages, and remediation efforts. Moreover, the indirect economic impacts of disrupted power supply can extend to businesses, industries, and communities reliant on uninterrupted electricity, resulting in economic losses and productivity declines.
Mitigating FDI Attacks
Secure communication protocols and encryption mechanisms:
Implementing strong encryption methods and secure communication protocols is essential for safeguarding data integrity and confidentiality. By ensuring that data transmitted within the smart grid network is encrypted and authenticated, the risk of unauthorized access and manipulation by attackers is significantly reduced.
Anomaly detection systems for early threat detection:
Deploying advanced anomaly detection algorithms enables early detection of abnormal behaviors or deviations from expected patterns within the smart grid system. These systems continuously monitor data from sensors and control devices, allowing for prompt identification of potential FDI attacks or other malicious activities. Examples include CNN (Convolutional Neural Network) and CUSUM (Cumulative Sum Algorithm).
Resilient control strategies to withstand manipulation:
Developing resilient control strategies that can adapt to changing conditions and resist manipulation by attackers is crucial for mitigating the impact of FDI attacks. By incorporating redundancy, diversity, and fault-tolerant mechanisms into control systems, the smart grid can maintain its functionality and stability even in the presence of malicious actors attempting to inject false data. Solutions such as quick intrusion detection algorithms, short-term state forecasting models, and adaptive sliding load control models can enhance the grid’s resilience against False data injection attacks.
In conclusion, safeguarding power systems, particularly within the context of smart grids, against cyber threats like false data injection (FDI) attacks is imperative for ensuring their reliable and uninterrupted operation. FDI attacks, along with other cyber threats, pose significant risks to the integrity, stability, and security of power distribution networks. However, through the implementation of robust defense mechanisms such as secure communication protocols, anomaly detection systems, and resilient control strategies, the impact of these attacks can be mitigated.
Moreover, addressing future challenges and considerations, including the evolving threat landscape, the importance of collaboration among industry stakeholders, and the need for continued innovation in cybersecurity measures, is essential. By staying vigilant, fostering collaboration, and embracing innovation, the power sector can effectively defend against cyber threats and ensure the resilience and reliability of smart grid infrastructure in the face of evolving risks.
Important Questions
Q:: What is a False Data Injection attack?
A:: A False Data Injection attack involves inserting counterfeit or deceptive information into a system to manipulate its operation.
Q:: Why are FDI attacks particularly concerning for power distribution systems?
A:: It can disrupt the normal operation of power distribution systems, potentially causing blackouts or grid instability.
Q:: How do FDI attacks exploit vulnerabilities in smart grid infrastructure?
A:: It exploit vulnerabilities in communication channels, sensors, and control mechanisms of smart grid infrastructure.
Q:: What are some characteristics of FDI attacks?
A:: Characteristics of FDI attacks include deception, manipulation of critical parameters, difficulty in detection, targeted exploitation, and disruption of normal operation.
Q:: What methods do attackers use to inject false data into smart grid systems?
A:: Attackers use methods such as Man-in-the-Middle attacks, sensor tampering, software exploitation, and insider threats to inject false data into smart grid systems.
Q:: What is the role of a State Estimator in power distribution networks?
A:: A State Estimator is a computational algorithm that estimates the current state of a power distribution network using data from various sensors and measurements.
Q:: How can false data injection affect the State Estimator?
A:: False data injection can manipulate power flow measurements within the State Estimator, creating inconsistencies and compromising its accuracy.
Q:: What is the SCADA system’s function in power distribution?
A:: The SCADA system collects real-time data from sensors, meters, and devices distributed throughout the power grid infrastructure.
Q:: How can FDI attacks impact the SCADA system?
A:: FDI attacks can manipulate power measurements and grid state transitions within the SCADA system, leading to inconsistencies in data and presenting fake grid states to operators.
Q:: What is the Smart Grid’s role in power distribution?
A:: The Smart Grid facilitates efficient and reliable power distribution by dynamically adjusting load control and power distribution mechanisms.
Q:: How can FDI attacks disrupt the Smart Grid’s operation?
A:: FDI attacks can alter dynamic loads and power bus parameters within the Smart Grid, leading to disruptions in load control and power distribution.
Q:: What are some implications of FDI attacks on power distribution systems?
A:: Implications of FDI attacks include grid instability, compromised operations and decision-making, and financial losses due to system downtime and economic impacts.
Q:: What are some strategies for mitigating FDI attacks?
A:: Strategies for mitigating FDI attacks include implementing secure communication protocols, deploying anomaly detection systems, and developing resilient control strategies.
Q:: How can encryption mechanisms help mitigate FDI attacks?
A:: Encryption mechanisms ensure data integrity and confidentiality, reducing the risk of unauthorized access and manipulation by attackers.
Q:: What is the importance of collaboration and innovation in defending against FDI attacks?
A:: Collaboration among industry stakeholders and continued innovation in cybersecurity measures are essential for effectively defending against FDI attacks and ensuring the resilience of power distribution systems.
Explore More:
Smart grid: https://plcdcscontrol.com/smart-grid-in-india/
IEEE Document on FDI: https://ieeexplore.ieee.org/document/8247663